Detection Engineering with Sigma
Detection Engineering is the process of researching threats and then building and tuning tools that find them.
Those tools come in several forms and include intrusion detection systems (IDS), log aggregators, antivirus engines, and a whole lot of fancy terms that basically mean math.
No matter the tool, they generally allow you to describe what you want to detect in a structured, specific way. Detection engineering is all about the craft of expressing what you want to detect in ways that are compatible with these detection mechanisms so that they can dig through evidence and find evil.
The alerts these tools generate are critical for identifying incidents. You need to write rules that are specific enough so that they don’t create a lot of false positives but broad enough that they are resilient and don’t require constant updates. You also need to write rules that are compatible with whatever search and detection mechanisms are available to you. That’s where popular open rule standards become valuable.
So far, analysts have depended on Snort and Suricata signatures for network traffic and YARA signatures for files. Now, we have Sigma.
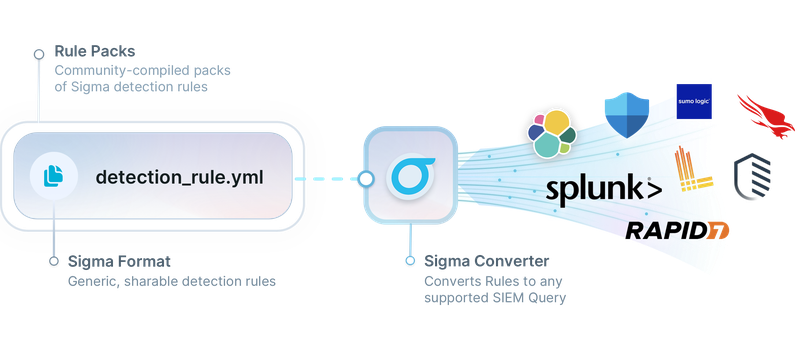
Sigma is the open standard signature format for logs.
The Sigma syntax provides a simple and powerful framework for expressing detection logic for diverse logs. You can use Sigma to write rules for detecting threats in countless log types: proxy logs, Windows events, application logs, firewall logs, cloud events, Linux audit logs, and many more.
Sigma provides the language necessary to describe detection logic and include metadata that’s helpful for investigating alerts generated from your rules. When you write detection rules with Sigma, you can better organize your rules and share those rules with colleagues and threat intel communities.
The most powerful feature of Sigma is that it was designed for compatibility with whatever search and detection tools you’re already using. You can use the Sigma converter tool to transform Sigma rules into Elastic, Splunk, Arcsight, Carbon Black, Graylog, NetWitness, Humio, Crowdstrike, Elastalert, and many other free and commercial formats. By storing your detection rules in Sigma syntax, you avoid vendor lock-in and gain the ability to use your detection logic across multiple detection tools, for searches in your investigations, and as a base for threat hunting queries.
While Sigma’s popularity has grown tremendously in the last few years, there has never been a course that takes a foundational approach to learning detection engineering through the lens of Sigma. It’s time to change that.
Now, I’m excited to offer an online course dedicated to teaching you how to interpret, build, and tune Sigma rules to become a better detection engineer or analyst.
Introducing…

Detection Engineering with Sigma will teach you how to write and tune Sigma rules to find evil in logs using real-world examples that take you through the detection engineering process.
We’ll dissect real Sigma detection rules focused on finding a variety of malicious activity in diverse log sources. Once you have a good handle on these components, you’ll start writing and tuning your own rules in a series of case studies. In some case studies, I’ll describe a detection gap and you’ll write a rule on your own before I show you how I tackled the problem myself. In other scenarios, you’ll write or modify a rule on your own and submit it to me for feedback.
In this course, you are never alone! I will be with you 100% of the way to help you understand the structure of Sigma rules, how to get from idea to finished rule, and best practices for writing resilient rules.
Along the way, you’ll learn...
- The detection engineering process from initial detection gap identification to deploying your rule.
- The structure of Sigma rules, including the difference between lists and maps, how condition expressions work, and all the essential metadata that’ll be useful for investigating alerts it generates.
- How to use the VSCode Sigma plugin to develop rules efficiently and with text-based helpers.
- Sigma-CLI usage to convert rules to popular investigation and detection tool formats like Splunk, ELK, and others.
- How to write resilient rules that find more evil, stand the test of time, and cause headaches for adversaries.
- How to write your own detection rules using familiar log sources like Windows Events, Zeek Logs, Sysmon Logs, AWS CloudTrail logs, and more.
- Guidelines and best practices for developing Sigma rules you can share with third parties, including the public Sigma rule repository.
- The principles of detection as code with a tutorial on managing your custom ruleset with Git.
- Tips and tricks for using Sigma and its tools on the command line.
- How to leverage popular Sigma integrations like Security Onion Playbook.
For this course, I created a virtual machine that contains all of the data you’ll need to follow along and participate in lab exercises. You’ll write Sigma rules and convert them to Kibana queries to test your detection against the sample data. You don’t need any previous Kibana experience to follow along with these labs and case studies.
If you want to enhance your detection engineering skills by mastering the open standard language for log-based detection, Detection Engineering with Sigma is the course you’re looking for.
You can view a detailed course syllabus here.
Detection Engineering with Sigma Includes
6 hours of demonstration videos. These videos will break down the concepts and skills you need to become adept at writing and tuning Sigma rules.
Hands-on labs to help you develop and test your skills. You’ll complete lab exercises by writing and modifying detection rules based on real-world detection gap scenarios.
Participation in our student charitable profit-sharing program. A few times a year, we designate a portion of our proceeds for charitable causes. AND students get to take part in nominating charities that are important to them to receive these donations.
Frequently Asked Questions
Is this course live?
This is NOT a live course. It’s an online video course you can take at your own pace.
How long do I have access to the course material?
You have access to the course for six months following your purchase date. If you need more time, you can extend your access for a small monthly fee.
Are there any prerequisites or lab requirements for this course?
This course is designed for all security practitioner skill levels and assumes no prior Sigma or detection engineering experience. We provide a virtual machine that allows you to follow along with the demonstrations and labs, along with the raw data so that you can follow along in your own environment if you like. To run the virtual machine for this course, your system should have:
- The ability to run a hypervisor such as VirtualBox or VMWare Player/Workstation/Fusion
- RAM: 3 GB (4 GB Recommended)
- CPU: 2 CPUs
- Hard Drive Space: 20 GB
How much time does it take to do this course?
Given the amount of content, it takes people dramatically different times to complete the material. If you focus all your time on it, you can complete everything in about a week. However, most choose to spread it out over a few weeks as they take time to practice the concepts demonstrated.
How many CPEs/CMUs is this course worth?
Organizations calculate continuing education credits in different ways, but they are often based on the length of the training. This course averages 12 hours of video+lab work.
Do you offer discounts for groups from the same organization?
Yes. To inquire about discounts or group invoices, please contact us at info@appliednetworkdefense.com.
Meet the Course Author - Josh Brower
Josh Brower has been crashing computers since his teens and now feels fortunate to be doing it professionally. He has spent the last decade+ focusing on InfoSec, particularly network and endpoint detection. He also enjoys teaching around InfoSec issues, especially to non-technical learners – helping them understand how their actions in the digital world have real-world consequences, and how to proactively reduce the risk.
You can catch him on Twitter at @DefensiveDepth.
Join Detection Engineering with Sigma Now for Just $397
Bulk discounts are available for organizations that want to purchase multiple licenses for this Sigma training course. Please contact us to discuss payment and pricing.